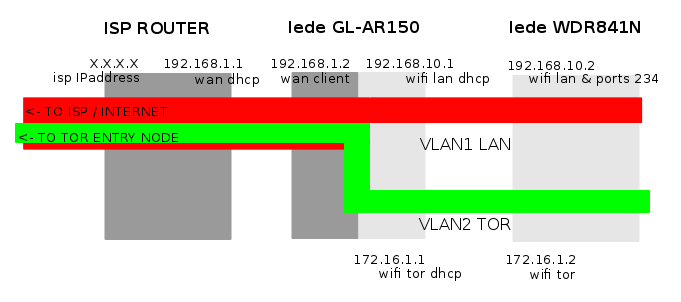
For an artistic project of mario, we prepared together a router which emits a wireless connection acting as a transparent proxy for The Onion Router project – TOR, leading your internet connection public IP through tor exit nodes drawing a spiral on the globe’s map, switching the exit node every 2 minutes.
We used a TP-Link archer c7 ver.2 router as hardware and played with lede’s configuration, tor and the crontab.
The dual band router emits a “normal” wireless network and a wireless network which acts as a transparent proxy to TOR, both networks in the 2.4 GHz and 5 Ghz range.
The internal networking of the router is divided in 3 vlans: wan (the connection leading to the internet) in dhcp client mode on the rear blue ethernet port, lan as a bridge (wifi access point and ethernet rear ports), and tor as a bridge (wifi access point only, configurable).
Prior to the configuration of this setup, you’ll need to:
- Connect your router to the internet and install the tor package:
opkg update
opkg install tor
- Enable cron:
/etc/init.d/cron enable
/etc/init.d/cron start
Basically, the crontab in /etc/root/crontab switches the configuration of the “/etc/tor/torrc” file and restarts tor at given times. Each “/etc/tor/torrc.X” file has a different “exit node country” code, forcing the “transparent tor proxy” running on the “tor wireless connection” to use an exit node from the country configured through the different “/etc/tor/torrc.X” files. To be able to check tor statuses, the torrc files are configured to store logs in “/var/log/tor/notices.log”, and to avoid general problems, I added a rule in the crontab to let the router reboot once every night.
Clicking on the next link you can download the FlagSwitcher.zip file with all the configuration files which differ from a standard lede 17.01 configuration for a Tp-Link Archer c7 ver 2 router.
Please remember that with a different router hardware, you’ll need first to fine tune “/etc/config/network” and subsequently “/etc/config/wireless” and “/etc/config/firewall” to match your router’s hardware characteristics.
The files involved in this configuration are:
- /etc/config/network
- /etc/config/wireless
- /etc/config/firewall
- /etc/config/dhcp
- /etc/tor/torrc
- /etc/crontabs/root
- /etc/firewall.user
## /etc/config/network
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config interface 'lan'
option type 'bridge'
option ifname 'eth0.1'
option proto 'static'
option ipaddr '192.168.90.1'
option netmask '255.255.255.0'
option _orig_ifname 'eth0.1 wlan0-1 wlan1-1'
option _orig_bridge 'true'
config interface 'wan'
option type 'bridge'
option ifname 'eth0.2'
option proto 'dhcp'
option _orig_ifname 'eth0.2 wlan0-2 wlan1-2'
option _orig_bridge 'true'
config interface 'tor'
option type 'bridge'
option ifname 'eth0.3'
option proto 'static'
option ipaddr '172.16.1.1'
option netmask '255.255.255.0'
option _orig_ifname 'eth0.3 wlan0 wlan1'
option _orig_bridge 'true'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option ports '0t 2 3 4 5 6t'
option vid '1'
config switch_vlan
option device 'switch0'
option vlan '2'
option ports '0t 1 6t'
option vid '2'
config switch_vlan
option device 'switch0'
option vlan '3'
option ports '0t 6t'
option vid '3'
## /etc/config/wireless
config wifi-device 'radio0'
option type 'mac80211'
option hwmode '11a'
option path 'pci0000:01/0000:01:00.0'
option htmode 'VHT80'
option channel 'auto'
option country 'ES'
config wifi-iface 'tor_radio0'
option device 'radio0'
option network 'tor'
option mode 'ap'
option ssid 'disrouting'
option encryption 'psk2+aes'
option key 'disrouting'
config wifi-iface 'lan_radio0'
option device 'radio0'
option network 'lan'
option mode 'ap'
option ssid 'lede'
option encryption 'psk2+aes'
option key 'FLAGswitch'
config wifi-device 'radio1'
option type 'mac80211'
option hwmode '11g'
option path 'platform/qca955x_wmac'
option htmode 'HT20'
option channel 'auto'
option country 'ES'
config wifi-iface 'tor_radio1'
option device 'radio1'
option network 'tor'
option mode 'ap'
option ssid 'disrouting'
option encryption 'psk2+aes'
option key 'disrouting'
config wifi-iface 'lan_radio1'
option device 'radio1'
option network 'lan'
option mode 'ap'
option ssid 'lede'
option encryption 'psk2+aes'
option key 'FLAGswitch'
## /etc/config/firewall
config defaults
option syn_flood 1
option input ACCEPT
option output ACCEPT
option forward REJECT
# Uncomment this line to disable ipv6 rules
option disable_ipv6 1
config zone
option name lan
list network 'lan'
option input ACCEPT
option output ACCEPT
option forward ACCEPT
config zone
option name wan
list network 'wan'
# list network 'wan6'
option input REJECT
option output ACCEPT
option forward REJECT
option masq 1
option mtu_fix 1
config zone
option name 'tor'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option network 'tor'
option conntrack '1'
config forwarding
option src lan
option dest wan
### TOR RULES
config rule
option name 'Allow-Tor-DHCP'
option src 'tor'
option proto 'udp'
option dest_port '67'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Tor-DNS'
option src 'tor'
option proto 'udp'
option dest_port '9053'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Tor-Transparent'
option src 'tor'
option proto 'tcp'
option dest_port '9040'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Tor-SOCKS'
option src 'tor'
option proto 'tcp'
option dest_port '9050'
option target 'ACCEPT'
option family 'ipv4'
# We need to accept udp packets on port 68,
# see https://dev.openwrt.org/ticket/4108
config rule
option name Allow-DHCP-Renew
option src wan
option proto udp
option dest_port 68
option target ACCEPT
option family ipv4
# Allow IPv4 ping
config rule
option name Allow-Ping
option src wan
option proto icmp
option icmp_type echo-request
option family ipv4
option target ACCEPT
config rule
option name Allow-IGMP
option src wan
option proto igmp
option family ipv4
option target ACCEPT
# Allow DHCPv6 replies
# see https://dev.openwrt.org/ticket/10381
config rule
option name Allow-DHCPv6
option src wan
option proto udp
option src_ip fc00::/6
option dest_ip fc00::/6
option dest_port 546
option family ipv6
option target ACCEPT
config rule
option name Allow-MLD
option src wan
option proto icmp
option src_ip fe80::/10
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family ipv6
option target ACCEPT
# Allow essential incoming IPv6 ICMP traffic
config rule
option name Allow-ICMPv6-Input
option src wan
option proto icmp
list icmp_type echo-request
list icmp_type echo-reply
list icmp_type destination-unreachable
list icmp_type packet-too-big
list icmp_type time-exceeded
list icmp_type bad-header
list icmp_type unknown-header-type
list icmp_type router-solicitation
list icmp_type neighbour-solicitation
list icmp_type router-advertisement
list icmp_type neighbour-advertisement
option limit 1000/sec
option family ipv6
option target ACCEPT
# Allow essential forwarded IPv6 ICMP traffic
config rule
option name Allow-ICMPv6-Forward
option src wan
option dest *
option proto icmp
list icmp_type echo-request
list icmp_type echo-reply
list icmp_type destination-unreachable
list icmp_type packet-too-big
list icmp_type time-exceeded
list icmp_type bad-header
list icmp_type unknown-header-type
option limit 1000/sec
option family ipv6
option target ACCEPT
# include a file with users custom iptables rules
config include
option path /etc/firewall.user
# allow IPsec/ESP and ISAKMP passthrough
config rule
option src wan
option dest lan
option proto esp
option target ACCEPT
config rule
option src wan
option dest lan
option dest_port 500
option proto udp
option target ACCEPT
## /etc/config/dhcp
config dnsmasq
option domainneeded '1'
option boguspriv '1'
option filterwin2k '0'
option localise_queries '1'
option rebind_protection '1'
option rebind_localhost '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option nonegcache '0'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option resolvfile '/tmp/resolv.conf.auto'
option localservice '1'
config dhcp 'lan'
option interface 'lan'
option start '100'
option limit '150'
option leasetime '12h'
# option dhcpv6 'server'
option ra 'server'
config dhcp 'tor'
option interface 'tor'
option start '100'
option limit '150'
option leasetime '12h'
config dhcp 'wan'
option interface 'wan'
option ignore '1'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
## /etc/tor/torrc
#Please notice that subsequent /etc/tor/torrc.X files only differ at the ExitNodes line, including different state codes
AllowUnverifiedNodes middle,rendezvous
VirtualAddrNetworkIPv4 172.16.1.0/11
AutomapHostsSuffixes .onion,.exit
AutomapHostsOnResolve 1
ExitNodes {de}
StrictNodes 1
GeoIPExcludeUnknown 1
MaxCircuitDirtiness 60
TransPort 9040
TransListenAddress 172.16.1.1
DNSPort 9053
DNSListenAddress 172.16.1.1
SocksPort 9050
SocksBindAddress 172.16.1.1:9050
Log notice file /var/log/tor/notices.log
## /etc/crontabs/root
#Please note that the first line will reboot the machine every day at 02.00 am, and that this is an example that you are invited to fullfill based on your own requirements, you’ll find my own full crontab in the above provided FlagSwitcher.zip file
00 2 * * * /bin/sleep 70 && /bin/touch /etc/banner && /sbin/reboot
00 * * * * /usr/bin/killall tor ; /bin/cp /etc/tor/torrc.1 /etc/tor/torrc ; /etc/init.d/tor restart
02 * * * * /usr/bin/killall tor ; /bin/cp /etc/tor/torrc.2 /etc/tor/torrc ; /etc/init.d/tor restart
04 * * * * /usr/bin/killall tor ; /bin/cp /etc/tor/torrc.3 /etc/tor/torrc ; /etc/init.d/tor restart
## /etc/firewall.user
tor_rules() {
iptables -t nat -A PREROUTING -i br-tor -p udp --dport 53 -j REDIRECT --to-ports 9053
iptables -t nat -A PREROUTING -i br-tor -p tcp --syn -j REDIRECT --to-ports 9040
}
tor_rules